I want to check the Mac connection status.
Asked 2 years ago, Updated 2 years ago, 67 views4 Answers
You can use the "Activity Monitor" in the utility folder for pre-installed items.
Double-click (or --I) the name of the application you want to launch and check for communication status, select the Open Files and Ports tab in the window that appears and wait for a while until the application lists open files, including ports and destination IP addresses.
However,
It's very hard to read.
When it comes to communication, it's Netstat.I thought there should have been a "network utility" in the utility folder that included Netstat before, so I searched Spotlight and found it now (after Mavericks) under /System/Library/CoreServices/Applications/.
To learn more about each tool and how to use it, open the network utility and select Network Utility Help from the Help menu.
However.
So Netstat is not related to each application, I forgot orz
If you want to capture packets, of course Wireshark is the best.However, installation is troublesome, and it has too many functions to use.If you want to check the connection, using Wireshark when you want to know what's communicating with you is an exaggeration.
In the See What Files&Ports an Application is Using with Activity Monitor I quoted earlier
The data is presented a little through, if you want an easy to browse version of open network connections take a look at the free GUI tool PrivateEye.
There was a comment saying that
This is the first application I've ever heard of, and it's quite useful.
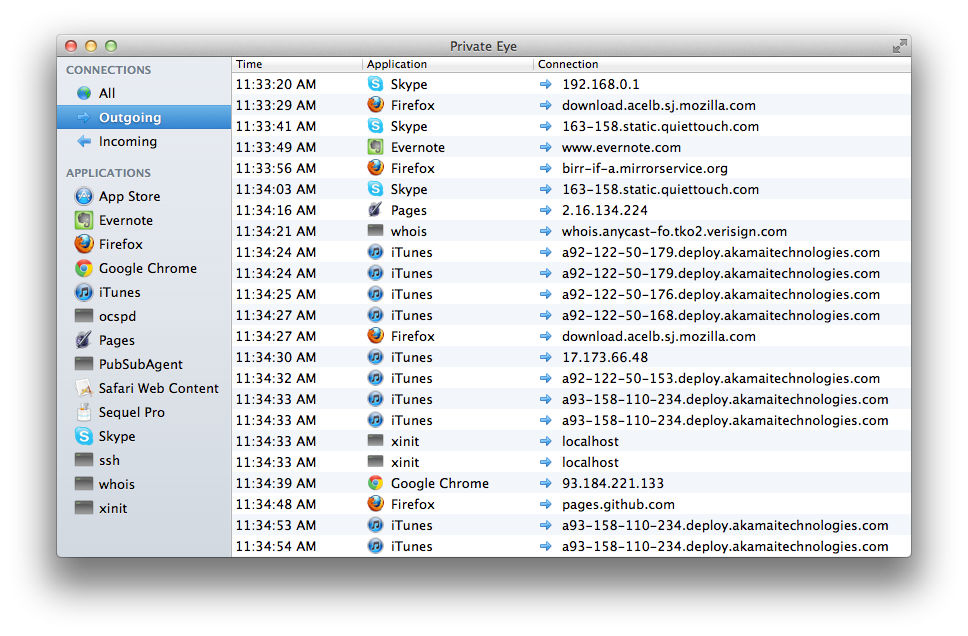
Displays the time and application name and destination (URL if name resolution is possible, IP address if not).The display items can then be sorted by time, application, and destination.You can also view all communications by specifying whether they are received, transmitted, or applications.
Private Eye is recommended.
(However, I am a little concerned about whether the sendsendsend has been captured. ReceiveOnly send...)
If you're using it in a terminal (command line), I think the lsof command is appropriate (or netstat), but it doesn't have the ability to display communication content only to the destination.
$sudolsof-iTCP-sTCP:ESTABLISHED
mplayer1466 nemo1007u IPv4 16684560t0 TCP nemo:39041->pub5.jazzradio.com:http (ESTABLISHED)
Firefox 19140 nemo 35u IPv4 16582920t0 TCP nemo: 50422->r-100-00-000-00.twttr.com:https (ESTABLISHED)
Firefox 19140 nemo 60u IPv4 16690840t0 TCP nemo:42877->stackoverflow.com:https (ESTABLISHED)
chrome 20695 nemo 108u IPv4 16968200t0 TCP nemo:53326->hogeXXsYY-in-fT.1ex00.net:https (ESTABLISHED)
mplayer20778 nemo1007u IPv4 16684560t0 TCP nemo:39041->pub5.jazzradio.com:http (ESTABLISHED)
Check man lsof for the lsof options.
If you want to know the contents of the communication, I think you can use a certain one.
If you want to know the details of the GUI, you can use Wireshark as well as Windows.
https://www.wireshark.org/download.html
It's troublesome to move it, so please refer to this area...
http://blog.pg1x.com/entry/2014/07/08/231557
I think it would be better to check the destination in Wireshark.
Below is the procedure.
Download and Install X11
http://xquartz.macosforge.org/landing/
Downloaded and installed Wireshark.
https://www.wireshark.org/download.html
When asked where to store the X11
/Applications/Utilities/XQuartz.app
It is stored in the , so it is specified.
Set access rights to the interface
sudo chmod0644/dev/bpf*
Specify the interface eth0 to capture, and
Press the start button to retrieve the communication log on the interface.

If you have any answers or tips
© 2024 OneMinuteCode. All rights reserved.